Security researchers from Carbon Black discovered malware campaigns embedded into MS Word macros. The report, indicated that it is distributing the Ursnif data-stealing malware, and the GandCrab ransomware.
The distribution of the malware starts with a phishing campaign, where malware infected Microsoft Word Documents are being attached to the phishing mails. Once the infected word document is invoked, a series of Powershell modules is used to download additional scripts, and this is where the fileless malware is delivered to the system. The malware would proceed to ex-filtrate data, and the ransomware would proceed on its ransomware behavior.
What is a fileless malware? A fileless malware exists in the RAM of computers and uses common system tools to inject malicious code into normally safe and trusted processes. It differs from a traditional malware as it does not have a footprint on the disk, as it only exists in memory. Because it does not touch the disk, it is hard to detect and remove. However, such malware will not be persistent if it only exist in the RAM, since rebooting the machine would effectively clear the RAM.
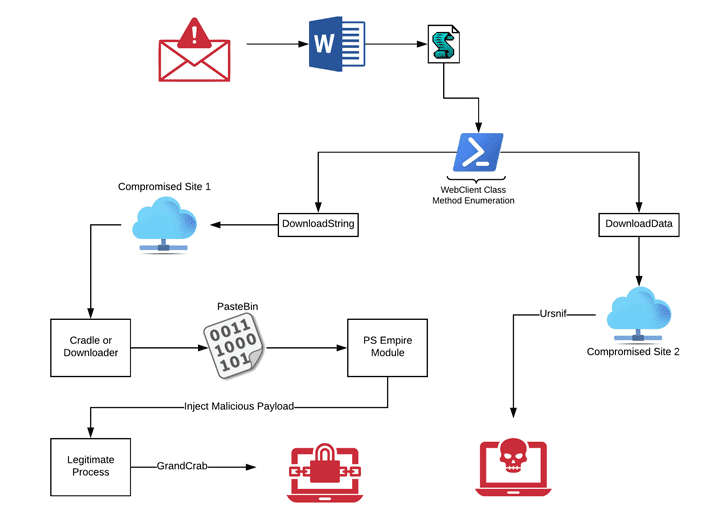
The result of the malicious word document would lead to data leakage, and machines falling victim to a ransomware. It is strongly encouraged to not open a word document from an unknown source which requires macro functionalities, unless it is from a trusted source. Threat actors today are finding new ways to break in, and the human factor is always the weakest link.